The Official Internet/Computer Security News Discussion Thread
#282
Needs more Lemon Pledge
Yeah! A six year old processor! Lol.
No spiders....
No spiders....

#284
Sweet!
iTrader: (1)
It was only a matter of time until OS X became a larger target for the baddies.
Luckily most of the people who use OS X at work are not so trusting. We had one user encounter Mac Defender but they were smart enough to not install the application. We swiftly sent out a mass e-mail about it and so far so good.
We'll be installing anti-virus software on all of our OS X systems this summer.
Luckily most of the people who use OS X at work are not so trusting. We had one user encounter Mac Defender but they were smart enough to not install the application. We swiftly sent out a mass e-mail about it and so far so good.
We'll be installing anti-virus software on all of our OS X systems this summer.
#285
Needs more Lemon Pledge

It was only a matter of time until OS X became a larger target for the baddies.
Luckily most of the people who use OS X at work are not so trusting. We had one user encounter Mac Defender but they were smart enough to not install the application. We swiftly sent out a mass e-mail about it and so far so good.
We'll be installing anti-virus software on all of our OS X systems this summer.
Luckily most of the people who use OS X at work are not so trusting. We had one user encounter Mac Defender but they were smart enough to not install the application. We swiftly sent out a mass e-mail about it and so far so good.
We'll be installing anti-virus software on all of our OS X systems this summer.
9CXwz.jpg
#287
Sweet!
iTrader: (1)
I don't know if it was mentioned here, but there are a number of free anti-virus applications out there for OS X. I've been running Sophos's free AV for a while now. I can't say that I've had any experience with clean-up, but other than an icon in the upper menu bar you don't even notice it's there. It's very light on resource usage. By default it checks for application & definition updates hourly.
It's supposed to be aware of the latest Mac Defender variants...I suppose I could go get infected and see at what point it stops me...
It's supposed to be aware of the latest Mac Defender variants...I suppose I could go get infected and see at what point it stops me...
#288
#289
Sanest Florida Man
Thread Starter
#290
Sanest Florida Man
Thread Starter

Google has removed over 11 million .co.cc websites from its search engine results pages on the basis that most of them are far too "spammy".
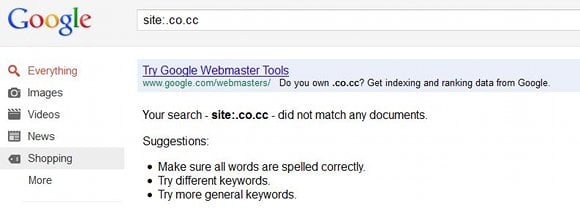
The .co.cc space is not an officially authorised second-level domain like .co.uk or .com.au. Rather, it's offered independently by a Korean company (http://co.cc/) that just happens to own the domain name .co.cc.
Google classes the firm as a "freehost", and has exercised its right to block the whole domain "if we see a very large fraction of sites on a specific freehost are spammy or low-quality", according to Matt Cutts, head of Google's web spam team.
The company said in a recent blog post: "To help protect users we recently modified those [malware-scanning] systems to identify bulk subdomain services which are being abused. In some severe cases our systems may now flag the whole bulk domain."
According to a recent report (29-page PDF/2MB) from the Anti-Phishing Working Group, the .cc top-level domain hosted 4,963 phishing attacks in the second half of 2010, almost twice the number found under any other extension.
That was due to a large number of attacks originating from .co.cc addresses, the APWG said.
The .co.cc "registry" offers single sub-domains for free, and enables customers to bulk-register 15,000 addresses at a time for a mere $1,000, or about seven cents a name.
The company claims to have 11,383,736 registered domains and 5,731,278 user accounts. That would make it one of the largest domain extensions in the world, bigger than both .org and .uk by over two million domains.
The .cc top-level domain belongs to the Cocos (Keeling) Islands, a small Australian territory in the Indian Ocean. Regular .cc websites are unaffected by Google's changes. ®

The .co.cc space is not an officially authorised second-level domain like .co.uk or .com.au. Rather, it's offered independently by a Korean company (http://co.cc/) that just happens to own the domain name .co.cc.
Google classes the firm as a "freehost", and has exercised its right to block the whole domain "if we see a very large fraction of sites on a specific freehost are spammy or low-quality", according to Matt Cutts, head of Google's web spam team.
The company said in a recent blog post: "To help protect users we recently modified those [malware-scanning] systems to identify bulk subdomain services which are being abused. In some severe cases our systems may now flag the whole bulk domain."
According to a recent report (29-page PDF/2MB) from the Anti-Phishing Working Group, the .cc top-level domain hosted 4,963 phishing attacks in the second half of 2010, almost twice the number found under any other extension.
That was due to a large number of attacks originating from .co.cc addresses, the APWG said.
The .co.cc "registry" offers single sub-domains for free, and enables customers to bulk-register 15,000 addresses at a time for a mere $1,000, or about seven cents a name.
The company claims to have 11,383,736 registered domains and 5,731,278 user accounts. That would make it one of the largest domain extensions in the world, bigger than both .org and .uk by over two million domains.
The .cc top-level domain belongs to the Cocos (Keeling) Islands, a small Australian territory in the Indian Ocean. Regular .cc websites are unaffected by Google's changes. ®
co.cc FTL I've seen lots of malware originating from there
#292
Sanest Florida Man
Thread Starter
never heard of it, wonder how good it is at detecting rootkits...
#293
Sanest Florida Man
Thread Starter
Just a heads up Adobe Reader 10.1 has a new automatic update feature that will update Reader in the background without relying on the user to update it manually! In windows it runs as a service called "armsvc.exe"
Unfortunately it's not set by default to run silently in the background you have to go to preferences > updater and choose "automatically install updates." The default is set to automatically download update but prompt the user to install them which is a fail because the user never bothers with it.
I will now be setting this to automatic on PCs I work on.
Also the autoupdate thing does work with XP
http://kb2.adobe.com/cps/908/cpsid_90886.html
On Windows 7, Vista, and Server 2008, Adobe Reader 10.1 installs ARMsvc.exe as part of the Updater. It is a Windows Service that runs in a System context. The new service enables silent and automatic updates on machines where a user has configured the application for automatic updates. (For automatic updates, choose Edit > Updater > Download And Install Updates Automatically or Preferences > Updater > Download And Install Updates Automatically.) Without this Service, the user confirms elevation through the User Account Control (UAC) dialog box during the update process.
I will now be setting this to automatic on PCs I work on.
Also the autoupdate thing does work with XP
http://kb2.adobe.com/cps/908/cpsid_90886.html
#294
Sanest Florida Man
Thread Starter
I swear I didn't plan this! As soon as I post the above post I go to neowin and see this!
http://www.neowin.net/news/six-out-o...eader-versions
Six out of ten users use vulnerable Adobe Reader versions

Avast Software, one of the biggest names in computer security have announced that six out of ten people are vulnerable to attacks through them having outdated versions of Adobe Reader.
What’s more worrisome is that hackers commonly use exploits in Adobe’s products which means this specific exploit is likely seen a high amount of usage.
Avast released a statement which said “an analysis of avast! antivirus users found that 60.2% of those with Adobe Reader were running a vulnerable version of the program and only 40% of users had the newest Adobe Reader X or were fullypatched. One out of every five users also had an unpatched version of Adobe Reader that was at least two generations old (8.x).”
The company later said “Adobe Reader is the most popular PDF reader application and subsequently is the biggest target for malware writers. Over 80% of avast! users run a version of Adobe Reader, with Foxit, the second most popular PDF reader, having a much smaller user share of 4.8%.”
Although the amount of Adobe Reader exploits has significantly dropped over the years, hackers are still targeting older versions because the usage of them collectively is extremely high. The 60% of unprotected users are being advised to download the latest version in order to defend themselves against any unsuspected attacks.
Adobe’s senior director of product security and privacy, Brad Arking was quoting as saying "we find that most consumers don’t bother updating a free app such as Adobe Reader as PDF files can be viewed in the older version. In many cases, users only update when provisioning a new machine," he said.

Avast Software, one of the biggest names in computer security have announced that six out of ten people are vulnerable to attacks through them having outdated versions of Adobe Reader.
What’s more worrisome is that hackers commonly use exploits in Adobe’s products which means this specific exploit is likely seen a high amount of usage.
Avast released a statement which said “an analysis of avast! antivirus users found that 60.2% of those with Adobe Reader were running a vulnerable version of the program and only 40% of users had the newest Adobe Reader X or were fullypatched. One out of every five users also had an unpatched version of Adobe Reader that was at least two generations old (8.x).”
The company later said “Adobe Reader is the most popular PDF reader application and subsequently is the biggest target for malware writers. Over 80% of avast! users run a version of Adobe Reader, with Foxit, the second most popular PDF reader, having a much smaller user share of 4.8%.”
Although the amount of Adobe Reader exploits has significantly dropped over the years, hackers are still targeting older versions because the usage of them collectively is extremely high. The 60% of unprotected users are being advised to download the latest version in order to defend themselves against any unsuspected attacks.
Adobe’s senior director of product security and privacy, Brad Arking was quoting as saying "we find that most consumers don’t bother updating a free app such as Adobe Reader as PDF files can be viewed in the older version. In many cases, users only update when provisioning a new machine," he said.
#295
Sanest Florida Man
Thread Starter
The reason I went to Neowin was to quote this article
pretty cool that they're working with gmail and yahoo on this too! I'd expect similar features from them in the future.
you can read more here:
http://windowsteamblog.com/windows_l...as-hacked.aspx
Hotmail introduces new security feature, 'My friend's account was hacked!'
One of the world leading email provides is stepping up their security for all their users. Since the beginning of email, spam has always been a problem that is very hard to combat.
As spammers continue to get smarter with their phishing emails, Hotmail is attempting to stay one step ahead. Hotmail is rolling out a new security feature that lets you help identify an email account as spam, called "My friend's been hacked!" Users may have already noticed this feature in Hotmail under the mark as dropdown.
The Windows Team Blog went in depth about how the feature works and how it helps keeps your friends email safe and secure. When a user receives a suspicious email from a friend, they mark the email as "My friend's been hacked!", which automatically puts all their emails into your junk folder.

The Hotmail team receives this complaint and combines it with information inside their spam detection engine and takes the necessary actions upon the account. In the case that an email actually has been hacked, Microsoft will lock down the account, preventing further spam from that account.
In order for your friends to re-active their account, they will have to follow and successfully complete the account recovery; make sure your account information is up to date and accurate.
The Hotmail team has also worked closely with Yahoo! and Gmail to also accept these reports and further investigate any suspicious activity on email accounts.
In addition to this new security feature, Microsoft is also preventing users from using common passwords like "password" and "123456". This will also include common phrases and words used by millions of people like "ilovecats". The feature won't require users to update their passwords if they use a common password, but going forward, this passwords will no longer be allowed.
One of the world leading email provides is stepping up their security for all their users. Since the beginning of email, spam has always been a problem that is very hard to combat.
As spammers continue to get smarter with their phishing emails, Hotmail is attempting to stay one step ahead. Hotmail is rolling out a new security feature that lets you help identify an email account as spam, called "My friend's been hacked!" Users may have already noticed this feature in Hotmail under the mark as dropdown.
The Windows Team Blog went in depth about how the feature works and how it helps keeps your friends email safe and secure. When a user receives a suspicious email from a friend, they mark the email as "My friend's been hacked!", which automatically puts all their emails into your junk folder.

The Hotmail team receives this complaint and combines it with information inside their spam detection engine and takes the necessary actions upon the account. In the case that an email actually has been hacked, Microsoft will lock down the account, preventing further spam from that account.
In order for your friends to re-active their account, they will have to follow and successfully complete the account recovery; make sure your account information is up to date and accurate.
The Hotmail team has also worked closely with Yahoo! and Gmail to also accept these reports and further investigate any suspicious activity on email accounts.
In addition to this new security feature, Microsoft is also preventing users from using common passwords like "password" and "123456". This will also include common phrases and words used by millions of people like "ilovecats". The feature won't require users to update their passwords if they use a common password, but going forward, this passwords will no longer be allowed.
you can read more here:
http://windowsteamblog.com/windows_l...as-hacked.aspx
#296
#297
Sanest Florida Man
Thread Starter
One of my clients today has Adobe Reader 6 installed...
Plus two different versions of Reader 8
I like that when I you install Reader X in automatically uninstalls any old versions of reader for you. It got rid of all three of the old versions

Plus two different versions of Reader 8
I like that when I you install Reader X in automatically uninstalls any old versions of reader for you. It got rid of all three of the old versions
#298
Sanest Florida Man
Thread Starter
Better late than never
ZWVha.png
These features shipped with Vista almost 5 years ago but it's nice to see it finally showing up on the world's most advanced operating system
http://www.apple.com/macosx/whats-ne....html#security
ZWVha.png
These features shipped with Vista almost 5 years ago but it's nice to see it finally showing up on the world's most advanced operating system
http://www.apple.com/macosx/whats-ne....html#security
#299
Sanest Florida Man
Thread Starter
Safari is now sandboxed in Lion too. This leaves Firefox as the last major browser to implement this making it the most insecure browser out there and that's why I don't recommend it and won't install it.
#300
Needs more Lemon Pledge
blah blah blah...
#301
So what you are saying sandbox builds a virtual cocoon in Chrome from windows calls?
Windows calls are pretty easy to circumvent. Best solution is to have a separately running VM...a hassle, but true security as which ever call they will run or attempt to call will fail.
About Reader, they always had some sort of vulnerability. I guess it's time to update. Thnx.
Windows calls are pretty easy to circumvent. Best solution is to have a separately running VM...a hassle, but true security as which ever call they will run or attempt to call will fail.
About Reader, they always had some sort of vulnerability. I guess it's time to update. Thnx.
#302
Sanest Florida Man
Thread Starter
So what you are saying sandbox builds a virtual cocoon in Chrome from windows calls?
Windows calls are pretty easy to circumvent. Best solution is to have a separately running VM...a hassle, but true security as which ever call they will run or attempt to call will fail.
About Reader, they always had some sort of vulnerability. I guess it's time to update. Thnx.
Windows calls are pretty easy to circumvent. Best solution is to have a separately running VM...a hassle, but true security as which ever call they will run or attempt to call will fail.
About Reader, they always had some sort of vulnerability. I guess it's time to update. Thnx.
this makes it difficult for malware that has inherited these rights from the app to actually doing anything malicious since it has no access to the system.
This IE's sandbox has been in windows for years and bypassing it's very rare, while it's possible (no software is perfect) when it does happen it's usually headline news in the security world because it's not a common occurrence.
#303
Ever tried this http://www.sandboxie.com/index.php?FirefoxTips ?
I personally rarely get viruses...almost never. I don't do random browsing, I have a few dedicated sites for all my needs. The only thing malware can mess with is my registry..which is the dumbest thing ever when it comes to security in Windows. Trojans and such won't work, I'm spoofed, behind two nats and vpns.
Right now the main concern I get from some of my clients is the phishing.. Many fell for this scheme and have paid dearly for it. So never click blindly on a link or even your bookmark without reassuring yourself.
I personally rarely get viruses...almost never. I don't do random browsing, I have a few dedicated sites for all my needs. The only thing malware can mess with is my registry..which is the dumbest thing ever when it comes to security in Windows. Trojans and such won't work, I'm spoofed, behind two nats and vpns.
Right now the main concern I get from some of my clients is the phishing.. Many fell for this scheme and have paid dearly for it. So never click blindly on a link or even your bookmark without reassuring yourself.
#304
Sanest Florida Man
Thread Starter
Is sandboxie still XP only? I know it doesn't work well with protected mode in Vista and it might not like ASLR either.
I don't get viruses either so I don't really worry enough to use sanboxie or a VM
edit: it's kernel patch protection and not ASLR that Sandboxie has an issue with and it does work with 7/vista now
I don't get viruses either so I don't really worry enough to use sanboxie or a VM
edit: it's kernel patch protection and not ASLR that Sandboxie has an issue with and it does work with 7/vista now
Last edited by #1 STUNNA; 07-19-2011 at 02:19 PM.
#305
the sandbox works by running giving the app very little rights or access to the system. It's not allowed to read or write to certain folders or the registry it's rights are lower than a standard user.
this makes it difficult for malware that has inherited these rights from the app to actually doing anything malicious since it has no access to the system.
This IE's sandbox has been in windows for years and bypassing it's very rare, while it's possible (no software is perfect) when it does happen it's usually headline news in the security world because it's not a common occurrence.
this makes it difficult for malware that has inherited these rights from the app to actually doing anything malicious since it has no access to the system.
This IE's sandbox has been in windows for years and bypassing it's very rare, while it's possible (no software is perfect) when it does happen it's usually headline news in the security world because it's not a common occurrence.
#306
Sanest Florida Man
Thread Starter
That scrub Charlie Miller is at it again!
http://blogs.forbes.com/andygreenber...pts-batteries/
At the Black Hat security conference in August, Miller plans to expose and provide a fix for a new breed of attack on Apple laptops that takes advantage of a little-studied weak point in their security: the chips that control their batteries.

Modern laptop batteries contain a microcontroller that monitors the power level of the unit, allowing the operating system and the charger to check on the battery’s charge and respond accordingly. That embedded chip means the lithium ion batteries can know when to stop charging even when the computer is powered off, and can regulate their own heat for safety purposes.
When Miller examined those batteries in several Macbooks, Macbook Pros and Macbook Airs, however, he found a disturbing vulnerability. The batteries’ chips are shipped with default passwords, such that anyone who discovers that password and learns to control the chips’ firmware can potentially hijack them to do anything the hacker wants. That includes permanently ruining batteries at will, and may enable nastier tricks like implanting them with hidden malware that infects the computer no matter how many times software is reinstalled or even potentially causing the batteries to heat up, catch fire or explode. “These batteries just aren’t designed with the idea that people will mess with them,” Miller says. “What I’m showing is that it’s possible to use them to do something really bad.”
Miller discovered the two passwords used to access and alter Apple batteries by pulling apart and analyzing a 2009 software update that Apple instituted to fix a problem with Macbook batteries. Using those keys, he was soon able to reverse engineer the chip’s firmware and cause it to give whatever readings he wanted to the operating system and charger, or even rewrite the firmware completely to do his bidding.
From there, zapping the battery such that it’s no longer recognized by the computer becomes trivial: In fact, Miller permanently “bricked” seven batteries just in the course of his tinkering. (They cost about $130 to replace.) More interesting from a criminal perspective, he suggests, might be installing persistent malware on the chip that infects the rest of the computer to steal data, control its functions, or cause it to crash. Few IT administrators would think to check a battery’s firmware for the source of that infection, and if undiscovered the chip could re-infect the computer again and again.
“You could put a whole hard drive in, reinstall the software, flash the BIOS, and every time it would reattack and screw you over. There would be no way to eradicate or detect it other than removing the battery.” says Miller.
That attack would require finding another vulnerability in the interface between the chip and the operating system. But Miller says that’s not much of a barrier. “Presumably Apple has never considered that as an attack vector, so it’s very possible it’s vulnerable.”
And the truly disturbing prospect of a hacker remotely blowing up a battery on command? Miller didn’t attempt that violent trick, but believes it might be possible. “I work out of my home, so I wasn’t super inclined to cause an explosion there,” he says.
In fact, the batteries he examined have other safeguards against explosions: fuses that contain an alloy that melts at high temperatures to break the circuit and prevent further charging. But Miller, who has worked for the National Security Agency and subsequently hacked everything from the iPhone to virtual worlds, believes it might still be possible. “You read stories about batteries in electronic devices that blow up without any interference,” he says. “If you have all this control, you can probably do it.”
Miller, currently a researcher with the consultancy Accuvant, isn’t the first to explore the danger of explosive batteries triggered by hackers. Barnaby Jack, a researcher for with antivirus giant McAfee, says he worked on the problem in 2009, but he says he ”benched the research when I didn’t succeed in causing any lithium ion fires. Charlie has taken it a lot further and surpassed where I was at the time.”
Miller says he’s received messages from several other researchers asking him not proceed with the battery work because it could be too dangerous. But Miller has worked to fix the problems he’s exposing. At Black Hat he plans to release a tool for Apple users called “Caulkgun” that changes their battery firmware’s passwords to a random string, preventing the default password attack he used. Miller also sent Apple and Texas Instruments his research to make them aware of the vulnerability. I contacted Apple for comment but haven’t yet heard back from the company.
Implementing Miller’s “Caulkgun” prevents any other hacker from using the vulnerabilities he’s found. But it would also prevent Apple from using the battery’s default passwords to implement their own upgrades and fixes. Those who fear the possibilities of a hijacked chunk of charged chemicals in their laps might want to consider the tradeoff.
“No one has ever thought of this as a security boundary,” says Miller. “It’s hard to know for sure everything someone could do with this.”

Modern laptop batteries contain a microcontroller that monitors the power level of the unit, allowing the operating system and the charger to check on the battery’s charge and respond accordingly. That embedded chip means the lithium ion batteries can know when to stop charging even when the computer is powered off, and can regulate their own heat for safety purposes.
When Miller examined those batteries in several Macbooks, Macbook Pros and Macbook Airs, however, he found a disturbing vulnerability. The batteries’ chips are shipped with default passwords, such that anyone who discovers that password and learns to control the chips’ firmware can potentially hijack them to do anything the hacker wants. That includes permanently ruining batteries at will, and may enable nastier tricks like implanting them with hidden malware that infects the computer no matter how many times software is reinstalled or even potentially causing the batteries to heat up, catch fire or explode. “These batteries just aren’t designed with the idea that people will mess with them,” Miller says. “What I’m showing is that it’s possible to use them to do something really bad.”
Miller discovered the two passwords used to access and alter Apple batteries by pulling apart and analyzing a 2009 software update that Apple instituted to fix a problem with Macbook batteries. Using those keys, he was soon able to reverse engineer the chip’s firmware and cause it to give whatever readings he wanted to the operating system and charger, or even rewrite the firmware completely to do his bidding.
From there, zapping the battery such that it’s no longer recognized by the computer becomes trivial: In fact, Miller permanently “bricked” seven batteries just in the course of his tinkering. (They cost about $130 to replace.) More interesting from a criminal perspective, he suggests, might be installing persistent malware on the chip that infects the rest of the computer to steal data, control its functions, or cause it to crash. Few IT administrators would think to check a battery’s firmware for the source of that infection, and if undiscovered the chip could re-infect the computer again and again.
“You could put a whole hard drive in, reinstall the software, flash the BIOS, and every time it would reattack and screw you over. There would be no way to eradicate or detect it other than removing the battery.” says Miller.
That attack would require finding another vulnerability in the interface between the chip and the operating system. But Miller says that’s not much of a barrier. “Presumably Apple has never considered that as an attack vector, so it’s very possible it’s vulnerable.”
And the truly disturbing prospect of a hacker remotely blowing up a battery on command? Miller didn’t attempt that violent trick, but believes it might be possible. “I work out of my home, so I wasn’t super inclined to cause an explosion there,” he says.
In fact, the batteries he examined have other safeguards against explosions: fuses that contain an alloy that melts at high temperatures to break the circuit and prevent further charging. But Miller, who has worked for the National Security Agency and subsequently hacked everything from the iPhone to virtual worlds, believes it might still be possible. “You read stories about batteries in electronic devices that blow up without any interference,” he says. “If you have all this control, you can probably do it.”
Miller, currently a researcher with the consultancy Accuvant, isn’t the first to explore the danger of explosive batteries triggered by hackers. Barnaby Jack, a researcher for with antivirus giant McAfee, says he worked on the problem in 2009, but he says he ”benched the research when I didn’t succeed in causing any lithium ion fires. Charlie has taken it a lot further and surpassed where I was at the time.”
Miller says he’s received messages from several other researchers asking him not proceed with the battery work because it could be too dangerous. But Miller has worked to fix the problems he’s exposing. At Black Hat he plans to release a tool for Apple users called “Caulkgun” that changes their battery firmware’s passwords to a random string, preventing the default password attack he used. Miller also sent Apple and Texas Instruments his research to make them aware of the vulnerability. I contacted Apple for comment but haven’t yet heard back from the company.
Implementing Miller’s “Caulkgun” prevents any other hacker from using the vulnerabilities he’s found. But it would also prevent Apple from using the battery’s default passwords to implement their own upgrades and fixes. Those who fear the possibilities of a hijacked chunk of charged chemicals in their laps might want to consider the tradeoff.
“No one has ever thought of this as a security boundary,” says Miller. “It’s hard to know for sure everything someone could do with this.”
#307
Team Owner
That attack would require finding another vulnerability in the interface between the chip and the operating system. But Miller says that’s not much of a barrier. “Presumably Apple has never considered that as an attack vector, so it’s very possible it’s vulnerable.”
Apple is now the 3rd largest PC vendor in the U.S. They own the tablet arena. Where is the onslaught of malware? Owait, they aren't a big enough of a target yet.
Last edited by doopstr; 07-23-2011 at 09:13 AM.
#308
Team Owner
So I read some other articles on this. Is he reprogramming the battery through OS X or not? Did I read the first thing I quoted incorrectly?  I still want to know when to expect my wife to brick my mac though. I thought the thing from a few months back was going to be the end of OS X.
I still want to know when to expect my wife to brick my mac though. I thought the thing from a few months back was going to be the end of OS X.
 I still want to know when to expect my wife to brick my mac though. I thought the thing from a few months back was going to be the end of OS X.
I still want to know when to expect my wife to brick my mac though. I thought the thing from a few months back was going to be the end of OS X.
Last edited by doopstr; 07-23-2011 at 11:54 AM.
#309
I just wanted to run this by everyone in case im missing something in my chain of thought.
When your using public unencrypted wifi on your laptop/phone, its safer to use logmein or team viewer to connect to home and use your home computer correct?
It makes it safe as all your traffic is going through the ssh tunnel. Are there any flaws using those tools? ex can wireshark or something still get my info? - i think its the safest way to use public wifi...
Or am i not considering everything here?
When your using public unencrypted wifi on your laptop/phone, its safer to use logmein or team viewer to connect to home and use your home computer correct?
It makes it safe as all your traffic is going through the ssh tunnel. Are there any flaws using those tools? ex can wireshark or something still get my info? - i think its the safest way to use public wifi...
Or am i not considering everything here?
#310
Sanest Florida Man
Thread Starter
You might want to go ahead and update to the latest version of Adobe Flash.

http://www.zdnet.com/blog/security/a...e_skin;content
Update it here:
http://get.adobe.com/flashplayer/
Adobe is fessing up to fixing much, much more than the 13 documented vulnerabilities in the latest critical Flash Player update.
Following an accusation from Google security researcher Tavis Ormandy that the company buried the fact that it patched a whopping 400 Flash Player vulnerabilities, Adobe security chief Brad Arkin (right) admitted the patch “contains about 80 code changes” for fix flaws identified by Ormandy’s team.
Following an accusation from Google security researcher Tavis Ormandy that the company buried the fact that it patched a whopping 400 Flash Player vulnerabilities, Adobe security chief Brad Arkin (right) admitted the patch “contains about 80 code changes” for fix flaws identified by Ormandy’s team.

http://www.zdnet.com/blog/security/a...e_skin;content
Update it here:
http://get.adobe.com/flashplayer/
#311
Sanest Florida Man
Thread Starter
Just a heads up Adobe Reader 10.1 has a new automatic update feature that will update Reader in the background without relying on the user to update it manually! In windows it runs as a service called "armsvc.exe"
Unfortunately it's not set by default to run silently in the background you have to go to preferences > updater and choose "automatically install updates." The default is set to automatically download update but prompt the user to install them which is a fail because the user never bothers with it.
I will now be setting this to automatic on PCs I work on.
Also the autoupdate thing does work with XP
http://kb2.adobe.com/cps/908/cpsid_90886.html
Unfortunately it's not set by default to run silently in the background you have to go to preferences > updater and choose "automatically install updates." The default is set to automatically download update but prompt the user to install them which is a fail because the user never bothers with it.
I will now be setting this to automatic on PCs I work on.
Also the autoupdate thing does work with XP
http://kb2.adobe.com/cps/908/cpsid_90886.html
#312
firefox 6 has that chrome tab close not re-size thing now. Finally its in firefox out of the box. Hated closing multiple tabs. hunting for the x.
#313
Sanest Florida Man
Thread Starter
^sweet!
#314
Team Owner
Here is a free training course on hacking web servers. I haven't had a chance to go through it myself, but hey, it's free! You don't even need to give them any information.
http://www.careeracademy.com/ceh-m12-launch.aspx
http://www.careeracademy.com/ceh-m12-launch.aspx
#315
Sanest Florida Man
Thread Starter
I'll look into it, thanks.
FYI, Microsoft killed the Botnet that was hosting the MacDefender malware so you might not have to worry about it anymore.....
http://www.zdnet.com/blog/security/m...e_skin;content
FYI, Microsoft killed the Botnet that was hosting the MacDefender malware so you might not have to worry about it anymore.....
Microsoft’s Digital Crimes Unit has shut down a botnet that was investigated for hosting the MacDefender scareware that preyed on Mac OS X users.
The botnet, known as Kelihos or “Waledac 2.0,” has been linked to spam messages, ID-theft attacks, pump-and-dump stock scams and websites promoting the sexual exploitation of children, according to Microsoft senior attorney Richard Domingues Boscovich.
The botnet contained about 41,000 computers worldwide and was capable of sending 3.8 billion spam e-mails per day.
The botnet, known as Kelihos or “Waledac 2.0,” has been linked to spam messages, ID-theft attacks, pump-and-dump stock scams and websites promoting the sexual exploitation of children, according to Microsoft senior attorney Richard Domingues Boscovich.
The botnet contained about 41,000 computers worldwide and was capable of sending 3.8 billion spam e-mails per day.
#316
Sanest Florida Man
Thread Starter
bump for inclusion in teh new forum
#317
Sanest Florida Man
Thread Starter
Microsoft Security Intelligence Report came out. The report provides threat trends and data analysis on topics like software vulnerabilities, exploits, malicious code and potentially unwanted software. It also covers third party products in the report.
QH7V9.png
Figure 2. Trends for vulnerability (CVE) severity, vulnerability complexity, disclosures by vendor, and disclosures by type
mDJqL.png
Ua6xm.png
vu6ps.png
2l4hx.png
CL9fP.png
Notice in the last graph almost all Reader and acrobat vulnerabilities exploit Javascript. (Win32/Pdfjsc) You can easily block these exploits by disabling Java in Reader preferences. I already described how in one of the first posts of this thread as seen below
Also got to updates and choose Automatically install updates in Reader/Acrobat preferences.
You can download the full report or just the summary here
http://www.microsoft.com/security/sir/default.aspx
Or just read the MS blog post about it for more info
http://blogs.technet.com/b/mmpc/arch...available.aspx
Also another good article about myths about Zero-days is here
http://www.zdnet.com/blog/security/s...;siu-container
QH7V9.png
In contrast to popular belief, this study found that zero-day vulnerabilities accounted for a very small percentage of actual infections. In fact, none of the top malware families detected through our tools like the Malicious Software Removal Tool and Microsoft Security Essentials, and others propagated through the use of a zero-day. And while some smaller families did take advantage of these types of vulnerabilities, less than 1 percent of all vulnerability attacks were against zero-day vulnerabilities – in other words, approximately 99% of attempted attacks impacted vulnerabilities for which an update was available.
mDJqL.png
Ua6xm.png
vu6ps.png
2l4hx.png
CL9fP.png
Notice in the last graph almost all Reader and acrobat vulnerabilities exploit Javascript. (Win32/Pdfjsc) You can easily block these exploits by disabling Java in Reader preferences. I already described how in one of the first posts of this thread as seen below
now for a little advice on how to configure Adobe Reader. Reader like most adobe software is riddled with security holes and they've been getting their ass handed to them as of late on the security front. There are some a couple settings you can change that will help this though.
If you open reader and go to preferences (ctrl + k) and
1. click on "Javascript" and turn off javascript.
2. Then go to "Trust Manager" and turn off "Allow opening of non-pdf file attachments with external applications"
Now if you're wondering if you should've had a holy shit WTF moment while reading the last two the answer is yes. By default reader allows javascript aka the java exploits I mentioned above to be run via PDF! As are external applications, so you open a PDF and it runs a malicious exe! WTF! Why does reader need to run java or external applications!?!?
I turned these off a few months ago and I'm glad that I did. Recently I was browsing a shady site and I moused over or accidentally clicked on a flash banner and bam! Reader opens up real fast with a blank PDF and this PDF wants to run Javascript! Luckily I had turned Java off for PDFs and so Reader was waiting for me to approve this PDF to run Java which I of course declined. Then the same thing happened a few days later. I wonder if I had java turned on would that blank empty PDF have even opened or would it have just done it's exploit in the background.
and I moused over or accidentally clicked on a flash banner and bam! Reader opens up real fast with a blank PDF and this PDF wants to run Javascript! Luckily I had turned Java off for PDFs and so Reader was waiting for me to approve this PDF to run Java which I of course declined. Then the same thing happened a few days later. I wonder if I had java turned on would that blank empty PDF have even opened or would it have just done it's exploit in the background.
As for downsides, I've yet to see a legit PDF prompt me to run Javascript or open an external application. So please do yourself the favor and turn those settings off.
If you open reader and go to preferences (ctrl + k) and
1. click on "Javascript" and turn off javascript.
2. Then go to "Trust Manager" and turn off "Allow opening of non-pdf file attachments with external applications"
Now if you're wondering if you should've had a holy shit WTF moment while reading the last two the answer is yes. By default reader allows javascript aka the java exploits I mentioned above to be run via PDF! As are external applications, so you open a PDF and it runs a malicious exe! WTF! Why does reader need to run java or external applications!?!?
I turned these off a few months ago and I'm glad that I did. Recently I was browsing a shady site
 and I moused over or accidentally clicked on a flash banner and bam! Reader opens up real fast with a blank PDF and this PDF wants to run Javascript! Luckily I had turned Java off for PDFs and so Reader was waiting for me to approve this PDF to run Java which I of course declined. Then the same thing happened a few days later. I wonder if I had java turned on would that blank empty PDF have even opened or would it have just done it's exploit in the background.
and I moused over or accidentally clicked on a flash banner and bam! Reader opens up real fast with a blank PDF and this PDF wants to run Javascript! Luckily I had turned Java off for PDFs and so Reader was waiting for me to approve this PDF to run Java which I of course declined. Then the same thing happened a few days later. I wonder if I had java turned on would that blank empty PDF have even opened or would it have just done it's exploit in the background.As for downsides, I've yet to see a legit PDF prompt me to run Javascript or open an external application. So please do yourself the favor and turn those settings off.
You can download the full report or just the summary here
http://www.microsoft.com/security/sir/default.aspx
Or just read the MS blog post about it for more info
http://blogs.technet.com/b/mmpc/arch...available.aspx
Also another good article about myths about Zero-days is here
http://www.zdnet.com/blog/security/s...;siu-container
The following users liked this post:
thelastaspec (12-11-2011)
#318
Sanest Florida Man
Thread Starter
So another exploit for Adobe Reader is making the news now a days, I read an article on ars and thought this was interesting.....
That's why you want to sandbox your apps, especially your web browsers....
http://arstechnica.com/tech-policy/n...o-day-hack.ars
Speaking of which....
Chrome sandboxing makes it the most secure browser, vendor study claims
This test also doesn't account for IE 9's Application Reputation or the fact that IE refuses to support WebGL because it gives untrusted code direct access to the GPU....
But interesting that Chromes sandbox may be better than IE9, I knew it was different but I just didn't know how.
And of course Firefox continues to suck when it comes to security.....
http://arstechnica.com/business/news...udy-claims.ars
Adobe has reported a new "critical vulnerability" for current and older versions of Adobe Reader and Acrobat for Windows, Mac OS X, and Unix operating systems. The attack has already been exploited by hackers in targeted attacks against the Adobe 9 reader on Windows, the company stated in its security advisory The hack appears to have already been used in an attack on US defense contractors and research facilities.
Discovered by Lockheed Martin's Computer Incident Response Team and MITRE, the vulnerability could allow an attacker to send a malicious Adobe document file that crashes Reader, and "potentiallty allow an attacker to take control of the affected system," according to the Adobe Product Security Incident Response Team's alert. In a blog post, Adobe's director of product security Brad Arkin said that Adobe is planning to release a fix for the Windows versions of Adobe Reader and Acrobat 9.4.6 "no later than the week of December 12." There is currently no workaround for Reader 9.x.
Arkin said that the risk to Mac OS X and Unix users of Reader is "significantly lower," and that the attack can be blocked on Windows with Reader X by opening documents in Adobe Reader X in "protected mode." Patches for those versions of Reader will be held until the next quarterly update of Reader, scheduled for January 10.
Arkin encouraged anyone still using Reader 9. "We put a tremendous amount of work into securing Adobe Reader and Acrobat X, and to date there has not been a single piece of malware identified that is effective against a version X install," he claimed. However, that would appear not to apply to Reader and Acrobat X users who open documents without using protected mode.
Discovered by Lockheed Martin's Computer Incident Response Team and MITRE, the vulnerability could allow an attacker to send a malicious Adobe document file that crashes Reader, and "potentiallty allow an attacker to take control of the affected system," according to the Adobe Product Security Incident Response Team's alert. In a blog post, Adobe's director of product security Brad Arkin said that Adobe is planning to release a fix for the Windows versions of Adobe Reader and Acrobat 9.4.6 "no later than the week of December 12." There is currently no workaround for Reader 9.x.
Arkin said that the risk to Mac OS X and Unix users of Reader is "significantly lower," and that the attack can be blocked on Windows with Reader X by opening documents in Adobe Reader X in "protected mode." Patches for those versions of Reader will be held until the next quarterly update of Reader, scheduled for January 10.
Arkin encouraged anyone still using Reader 9. "We put a tremendous amount of work into securing Adobe Reader and Acrobat X, and to date there has not been a single piece of malware identified that is effective against a version X install," he claimed. However, that would appear not to apply to Reader and Acrobat X users who open documents without using protected mode.
http://arstechnica.com/tech-policy/n...o-day-hack.ars
Speaking of which....
Chrome sandboxing makes it the most secure browser, vendor study claims
A new study by security vendor Accuvant Labs concludes that Google Chrome is more secure than rivals Firefox and Internet Explorer, largely because of Chrome's sandboxing and plug-in security.
The research was funded by Google, which might make any reasonable person suspicious of its conclusions. Accuvant insists that Google gave it "a clear directive to provide readers with an objective understanding of relative browser security" and that the conclusions in the paper "are those of Accuvant Labs, based on our independent data collection." Accuvant also made the supporting data available as a separate download so that it can be scrutinized by other researchers.
Accuvant focused only on Chrome, IE and Firefox, leaving out Safari and others for the sake of time. It also tested the browsers only on Windows 7, 32-bit edition. Despite concluding research in July, the paper was just released today. As a result, the report excludes newer versions of Chrome and Firefox, which have more rapid release cycles than Internet Explorer.
But the 102-page report otherwise seems fairly thorough, and Accuvant says it will update the report as the security of each browser evolves, and claims that it already provides a better look at browser security than metrics such as vulnerability report counts and URL blacklists. "We believe an analysis of anti-exploitation techniques is the most effective way to compare security between browser vendors," the report states. "This requires a greater depth of technical expertise than statistical analysis of CVEs, but it provides a more accurate window into the vulnerabilities of each browser."
A chart summarizing Accuvant's conclusions shows the vendor believes Google's sandboxing and plug-in security exceeds that of Internet Explorer, and that Google at least matches Firefox and IE in other types of security. In this chart, DEP refers to data execution prevention, GS is a compiler switch used to prevent buffer overflows, ASLR stands for Address Space Layout Randomization, and JIT stands for "just in time" compilation, which is used to improve runtime performance.

"The URL blacklisting services offered by all three browsers will stop fewer attacks than will go undetected," Accuvant states. "Both Google Chrome and Microsoft Internet Explorer implement state-of-the-art anti-exploitation technologies, but Mozilla Firefox lags behind without JIT hardening. While both Google Chrome and Microsoft Internet Explorer implement the same set of anti-exploitation technologies, Google Chrome’s plug-in security and sandboxing architectures are implemented in a more thorough and comprehensive manner. Therefore, we believe Google Chrome is the browser that is most secured against attack."
Microsoft might point to a report from NSS Labs, which has found that Internet Explorer far exceeds its rivals in blocking malware. However, some of NSS Labs' research has been funded by Microsoft.
The Accuvant report says Chrome's sandboxing "uses a medium integrity broker process that manages the UI, creates low integrity processes and further restricts capabilities by using a limited token for a more comprehensive sandbox than the standard Windows low integrity mechanism... The extensive use of sandboxing limits both the available attack surface and potential severity of exploitation."
Internet Explorer, by contrast, has processes that allow compromised tabs some ability to infect other tabs, Accuvant says. "In the event of a crash, the tab [in Internet Explorer] is automatically reloaded the first time, allowing malicious content multiple attempts to succeed, or have an unsuccessful exploit attempt go unnoticed," Accuvant claims. "A tab compromised by an exploit would have read access to the file system and any low integrity process, including other browser tabs. The compromised process would need a method of privilege escalation from low integrity to persist beyond the browser session."
With Firefox, Accuvant states, simply, that it has no sandboxing and "A compromised browser or plug-in process would not require privilege escalation to persist beyond the browser process."
Google has long touted the robustness of its sandboxing, although security researchers claimed to have subverted Chrome's sandbox earlier this year. Microsoft touts its own security and privacy features, as does Mozilla. The Register notes some anecdotal evidence supports the claim that Chrome is most secure, including the fact that "Chrome has emerged unscathed during the annual Pwn2Own hacker contest for three years in a row, something no other browser entered has done." Ultimately, the question of which browser is safest is still up for debate. What do you think?
The research was funded by Google, which might make any reasonable person suspicious of its conclusions. Accuvant insists that Google gave it "a clear directive to provide readers with an objective understanding of relative browser security" and that the conclusions in the paper "are those of Accuvant Labs, based on our independent data collection." Accuvant also made the supporting data available as a separate download so that it can be scrutinized by other researchers.
Accuvant focused only on Chrome, IE and Firefox, leaving out Safari and others for the sake of time. It also tested the browsers only on Windows 7, 32-bit edition. Despite concluding research in July, the paper was just released today. As a result, the report excludes newer versions of Chrome and Firefox, which have more rapid release cycles than Internet Explorer.
But the 102-page report otherwise seems fairly thorough, and Accuvant says it will update the report as the security of each browser evolves, and claims that it already provides a better look at browser security than metrics such as vulnerability report counts and URL blacklists. "We believe an analysis of anti-exploitation techniques is the most effective way to compare security between browser vendors," the report states. "This requires a greater depth of technical expertise than statistical analysis of CVEs, but it provides a more accurate window into the vulnerabilities of each browser."
A chart summarizing Accuvant's conclusions shows the vendor believes Google's sandboxing and plug-in security exceeds that of Internet Explorer, and that Google at least matches Firefox and IE in other types of security. In this chart, DEP refers to data execution prevention, GS is a compiler switch used to prevent buffer overflows, ASLR stands for Address Space Layout Randomization, and JIT stands for "just in time" compilation, which is used to improve runtime performance.

"The URL blacklisting services offered by all three browsers will stop fewer attacks than will go undetected," Accuvant states. "Both Google Chrome and Microsoft Internet Explorer implement state-of-the-art anti-exploitation technologies, but Mozilla Firefox lags behind without JIT hardening. While both Google Chrome and Microsoft Internet Explorer implement the same set of anti-exploitation technologies, Google Chrome’s plug-in security and sandboxing architectures are implemented in a more thorough and comprehensive manner. Therefore, we believe Google Chrome is the browser that is most secured against attack."
Microsoft might point to a report from NSS Labs, which has found that Internet Explorer far exceeds its rivals in blocking malware. However, some of NSS Labs' research has been funded by Microsoft.
The Accuvant report says Chrome's sandboxing "uses a medium integrity broker process that manages the UI, creates low integrity processes and further restricts capabilities by using a limited token for a more comprehensive sandbox than the standard Windows low integrity mechanism... The extensive use of sandboxing limits both the available attack surface and potential severity of exploitation."
Internet Explorer, by contrast, has processes that allow compromised tabs some ability to infect other tabs, Accuvant says. "In the event of a crash, the tab [in Internet Explorer] is automatically reloaded the first time, allowing malicious content multiple attempts to succeed, or have an unsuccessful exploit attempt go unnoticed," Accuvant claims. "A tab compromised by an exploit would have read access to the file system and any low integrity process, including other browser tabs. The compromised process would need a method of privilege escalation from low integrity to persist beyond the browser session."
With Firefox, Accuvant states, simply, that it has no sandboxing and "A compromised browser or plug-in process would not require privilege escalation to persist beyond the browser process."
Google has long touted the robustness of its sandboxing, although security researchers claimed to have subverted Chrome's sandbox earlier this year. Microsoft touts its own security and privacy features, as does Mozilla. The Register notes some anecdotal evidence supports the claim that Chrome is most secure, including the fact that "Chrome has emerged unscathed during the annual Pwn2Own hacker contest for three years in a row, something no other browser entered has done." Ultimately, the question of which browser is safest is still up for debate. What do you think?
But interesting that Chromes sandbox may be better than IE9, I knew it was different but I just didn't know how.
And of course Firefox continues to suck when it comes to security.....
http://arstechnica.com/business/news...udy-claims.ars
Last edited by #1 STUNNA; 12-09-2011 at 09:49 PM.
The following users liked this post:
thelastaspec (12-11-2011)
#319
Sanest Florida Man
Thread Starter
OK this is a serious hack! Some one has hacked WPS on routers and they can get into your wifi network within a couple hours using bruteforce attack.
WPS stand for Wireless Protected Setup. You push the WPS button on your router and type in the 8 digit WPS passcode when prompted on your PC and it joins your PC automatically and enters the wifi password for you. I think it's really annoying and have never used it, but anyway it's there.
It uses a unique 8 digit code which gives it 100 million possibilities (0-99999999) which would take years to crack. Well apparently WPS isn't that "protected" the router will actually tell you when the first 4 digits of the passcode are correct!! So this cuts the possible remaining numbers from 100 million to two groups of 10,000! So your brute force the first 4 digits and once you get it the router lets you know those are correct and then you start on the last 4 digits while using the first 4 you just found. So with a couple hours of bruteforce you can get any PC onto the network and get you the Wifi password!
There have been a couple different sets of tools to do so released on the interwebs
Here's a video of the hack and how it works
<iframe src="http://player.vimeo.com/video/34402962?title=0&byline=0&portrait=0" width="400" height="225" frameborder="0" webkitAllowFullScreen mozallowfullscreen allowFullScreen></iframe><p><a href="http://vimeo.com/34402962">wpscrack vs. TP-Link TL-WR1043ND - Demo</a> from <a href="http://vimeo.com/user4946894">Stefan Viehboeck</a> on <a href="http://vimeo.com">Vimeo</a>.</p>

Ars did an article about it and got it to work. It even worked AFTER turning WPS OFF! Apparently the Linksys router still responded to WPS requests even though the feature was disabled on the router settings page. So there is apparently no workaround except if the router doesn't support WPS.
My Netgear WNDR 3700 supports WPS but I use DD-WRT on it and IDK if it supports WPS. I guess you can disable WPS (it's worthless anyways) and maybe that will work at actually disabling it but if not you're SOL until there's a firmware upgrade to your router that fixes this.
Read more here: http://arstechnica.com/business/news...ith-reaver.ars
Get the tools here: http://sviehb.wordpress.com/2011/12/...vulnerability/
WPS stand for Wireless Protected Setup. You push the WPS button on your router and type in the 8 digit WPS passcode when prompted on your PC and it joins your PC automatically and enters the wifi password for you. I think it's really annoying and have never used it, but anyway it's there.
It uses a unique 8 digit code which gives it 100 million possibilities (0-99999999) which would take years to crack. Well apparently WPS isn't that "protected" the router will actually tell you when the first 4 digits of the passcode are correct!! So this cuts the possible remaining numbers from 100 million to two groups of 10,000! So your brute force the first 4 digits and once you get it the router lets you know those are correct and then you start on the last 4 digits while using the first 4 you just found. So with a couple hours of bruteforce you can get any PC onto the network and get you the Wifi password!
There have been a couple different sets of tools to do so released on the interwebs
Here's a video of the hack and how it works
<iframe src="http://player.vimeo.com/video/34402962?title=0&byline=0&portrait=0" width="400" height="225" frameborder="0" webkitAllowFullScreen mozallowfullscreen allowFullScreen></iframe><p><a href="http://vimeo.com/34402962">wpscrack vs. TP-Link TL-WR1043ND - Demo</a> from <a href="http://vimeo.com/user4946894">Stefan Viehboeck</a> on <a href="http://vimeo.com">Vimeo</a>.</p>

Ars did an article about it and got it to work. It even worked AFTER turning WPS OFF! Apparently the Linksys router still responded to WPS requests even though the feature was disabled on the router settings page. So there is apparently no workaround except if the router doesn't support WPS.
My Netgear WNDR 3700 supports WPS but I use DD-WRT on it and IDK if it supports WPS. I guess you can disable WPS (it's worthless anyways) and maybe that will work at actually disabling it but if not you're SOL until there's a firmware upgrade to your router that fixes this.
Read more here: http://arstechnica.com/business/news...ith-reaver.ars
Get the tools here: http://sviehb.wordpress.com/2011/12/...vulnerability/
Last edited by #1 STUNNA; 01-09-2012 at 06:46 PM.
#320
What programs (if any) does everyone use for prevention? Like stopping infections before they begin?
Do you use something for your PC, and then something different for others that you work on?
I've put SpywareBlaster on my brother-in-law's PC recently, basically trying it out.
http://www.javacoolsoftware.com/spywareblaster.html
Anyone else use it? Thoughts? Or recommend something else to try?
Do you use something for your PC, and then something different for others that you work on?
I've put SpywareBlaster on my brother-in-law's PC recently, basically trying it out.
http://www.javacoolsoftware.com/spywareblaster.html
Anyone else use it? Thoughts? Or recommend something else to try?



 I've seen the same thing!
I've seen the same thing!